Been a fun week.
Been see a lot of warnings
like this latelyStill not clear on who ml314.com is but their cert is expired and blocking them seems to have no affect so I did. Same with the other expired certs that came up. If you see a pop up telling you cert is iffy block it. If you have other blocking tools add that domain.
Then I saw a lot of warnings about a known JavaScript miner site being included in sites I'm visiting. Nothing that weird either. The site is t.hanstrackr.com After I explicitly blocked the JavaScript I got a warning it was trying an HTML method from my antivirus!
Then I see this article when looking for why the extension got disabled
Google cuts fake ad blockers from Chrome Store: Were you among 20 million fooled?Adremover, the one I was using, was the most downloaded of the ad blockers in the extension store. It was downloaded by 10 million! It also was blocking so much stuff that I had to keep turning it off to use a lot of sites. I'm not sure how long Adremover was off before I noticed but I think all the expired cert warning started about the same time. So I'm not sure calling it a "fake" ad blocker is exactly accurate.
As a stop gap I upped my OpenDNS filtering to include "Adware" and "Hate/Discrimination" though it does not seem to be stopping all that much.
I'm guessing that is because so many sites are moving code to sites on blocked lists and adding other blocker detector to try and force us to turn them off. Note I have no problem with ads as long as they are vetted for malware and do not slow the page loads to a crawl but responsible advertising seems to be mighty rare these days.
I upgraded my internet:
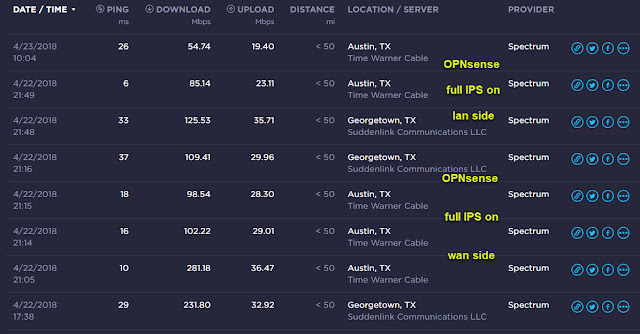
With just my workstation plugged into the modem I'm not really seeing much of an improvement in download speed but upload is better than expect and that was my bottleneck. The cable guy's meter was showing over 900 Mbps down but I did notice it jumped up from ~350 to over 900 close to the end of the test so it is probably a burst speed more than a solid speed. This seems to confirm what I'm seeing. New Spectrum GIG no where near 940 Mbps But then I do not see buffering watching HD content even while running speed tests and downloading updates all at the same time so I don't think download speed will prove to be an issue anytime soon.There was a bit of a mix up and Starz was not in the bundle I got so had to add that again. Still ended up adding Showtime, Cinemax and Starz plus doubling my upload speed for less than $20 more a month. Not bad. One weird bit though is I seem to have lost channel 511, HBO HD east. They have no clue why. Error says temp issue so maybe will sort on its own. Since I almost never watch live, picking up on the west feed is not biggie.
The new internet setup is kind of strange too. They bring out a modem AND a router. Seems you do not need to use their router and it does not have the phone interface so you need to keep the old modem/router as well just for the phone. Instead of using their router I think I'll stick a pfSense box instead. I was planning on adding one anyway later. I'll need to rewire some stuff though so I'll be on and off probably for the rest of this weekend.
I put one of my old NETGEAR Nighthawk R7000 from before my Unifi conversion in place while I got OPNsense installed This turned out to be VERY bad for throughput but at least I had some protection while I got OPNsense ready.
So now I'm setting up OPNsense.
From what I'm reading in forums and groups, OPNsense is a fork / more user friendly version of pfSense so I decide to go with it. Also see pfSense® vs OPNsense®: technical comparison and this compare from a guy that installed both. One of the co-founders of pfSense joined Unifi awhile back and the additions they are now making to Unifi fall somewhere in between OPNsense and pfSense from what I as a user see. As I mention below though it seems unlikely current Unifi hardware will be able handle the load of processing high bandwidth data so going with a standalone box makes more sense for probably at least the next year.I'm using a Dell 745 with an Intel(R) Core(TM)2 CPU 6400 @ 2.13GHz (2 cores), CDROM drive, 2 TB HD and 8 GB RAM. It is just spare I had been using initially for OpenShift testing but is not really powerful enough for any real projects I do these days but well beyond what a Unifi USG can do with a dual-core, 500 MHz processor, 512 MB DDR2 RAM and 2 GB of storage.
Install went smooth (the occasional label did not match the instructions but it was generally obvious what to do next) except for one thing. The DVD image failed half way though coming up because it seemed to be unable to find the USB DVD drive I had booted from. I had even less luck with a USB stick image as they would not even boot but that might have more to do with the age of the PC I'm using. Note when installer the new machine I found the installer went through without error the second time but got the same CD not found error the first time so this might just be an intermittent issue.
Even more detailed instructions can be found in Building a BSD home router (pt. 5): Installing OPNsense
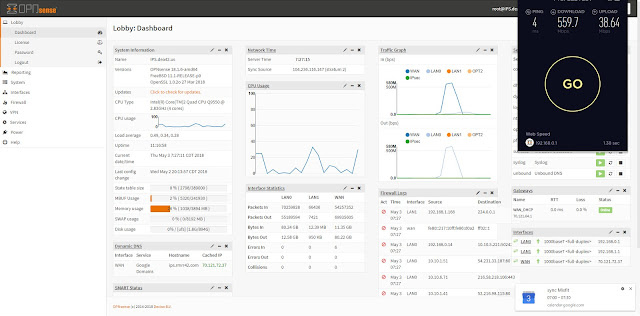
From the picture above you can see It performed well as a router even after turning off hardware offloading but when I turned on full IPS it took a real hit.
The CPU usage is frequently hitting 100% though so I think that is at least part of the problem. I'll need to try swapping in a Dell 780 with a Intel(R) Core(TM)2 Quad CPU Q9550 @ 2.83GHz box and see it that improves things. For now though it mainly seems to be affecting download and upload so not pressing. This is what the dashboard looks like (WAN IP blacked out here of course).
Just unchecking IPS mode on the OPNsense Services: Intrusion Detection: Administration page, but leaving IDS enabled, pretty much gets us back to normal.
Having IPS on was also causing check for updates to fail.
Reports
Traffic
So far the traffic reports look about the same as what I'd get from Unifi though in my case it helps me to filter just what is talking or not talking to the outside world. Otherwise Unifi pretty much wins here.IPS
Now this is the bit I wanted OPNsense for. Unifi has started adding much of this in but with the CPU their routers have it just can't cope with processing this amount of data. Turning IPS on with the low end USG router people are reporting download speeds in the 50 Mbps range. As mentioned above even the Dual core I'm using for OPNsense is struggling with full IPS on (29905 rules) and drastically reduced max speeds. Granted that many rules is probably over kill. Especially when looking at the alert log and seeing almost all the hits were for this one rule
Unifi has a similar geo filter but currently you can only have on where OPNsense lets you have many.
Both let you get just alerts or drop packets. Note the above test had both set to alert instead of drop. Unifi set to alert only mode hardly affected throughput at all while block mode definitely does. With OPNsense it was not as clear because setting IPS mode on here
Seems drag down the system as if packets are being block even though the rules themselves have their "Action" set to Alert. Though looking at the above Unifi rule that would seem to imply it is blocking these packets yet OPNsense is still seeing them would imply it is working similar. But then too the only IPS alerts I've seen from Unifi since turning alerts on are:
EVENT TIME
IPS Alert 2: Misc Attack. Signature ET DROP Dshield Block Listed Source group 1. From: 191.101.167.73:46524, to: 10.10.2.48:8078, protocol: TCP, in interface: eth1 11:30 04/18/2018
IPS Alert 2: Misc Attack. Signature ET DROP Dshield Block Listed Source group 1. From: 191.101.167.37:46430, to: 10.10.2.46:8076, protocol: TCP, in interface: eth1 19:12 04/11/2018
An IP that appears to be in Netherlands though the attached phone number and some of the contact info is Czech.
My Unifi IPS setting look like this
Console
Have to say I like the amount of stuff you can cram onto the console. Her I have it in 4 column mode and this is not even everything you can stick on there. Surprised there seems to be no way to hide or shrink the left nav menu as customizable as the rest is.
ssh access
Seems checking Permit password login does not seem to work. You still need to use ssh keys.Adding speedtest to the OPNsesnse box
This should work but did not for mecurl -Lo speedtest-cli https://raw.githubusercontent.com/sivel/speedtest-cli/master/speedtest.py
chmod +x speedtest-cli
So as a work around I copy pasted into vi from a browser. Note you will need to change the first line from python to python2.7 either way so it can find the python command.
Run it like this
For keeping track create a cron job that writes to a csv file
As root run (changing 16089 to the server ID you want to test against)/root/speedtest-cli --server 16089 --csv-header > /usr/local/www/speedtest.csv
That sets the headers for you
Update it appears the crontab is getting overwritten so you may have to redo this from time to time.
To avoid this you need to create a /usr/local/opnsense/service/conf/actions.d/actions_speedtest.conf file and add
[test]
command:/root/speedtest-cli --server 16089 --csv >> /usr/local/www/speedtest.csv
description:Run a speed test
parameters:%s
type:script
message:running speed test %s
After saving run
service configd restart
to load action file changes then
configctl speedtest test
to test it. You should get an OK as a response. Then add as a cron job through the web GUI like this
This should add a line to the crontab but does not seem too. Nor did it run at first even after reboot but then started running later. No obvious reason why but the line I manually added to the crontab disappeared about the same time. Still not adding a line in crontab though so being handled else where.
Odd bits
Sometimes the Speedtest.net extension just seems to hang when run while on the dashboard page.
As mentioned above check updated fails with IPS on. It appeared it was because the Core(TM)2 CPU is just not powerful enough to handle both at the same time. But I'm seeing the same with the Quad Core and the CPU is under 40% max.
I found a good starting point for rules in this pfSense post
Basically this sets:
- emerging-drop
- emerging-botcc.portgrouped
- emerging-botcc
- emerging-ciarmy
- emerging-compromised
- emerging-dshield
- emerging-tor
- emerging-worm
- emerging-trojan
- emerging-mobile_malware
- emerging-malware
- snort
Note on Snort. There are a lot of Snort rules. I filtered the list for "snort", selected all then enabled selected which enabled about half of them. I then also enabled Snort VRT/blacklist.
After reenabling IPS mode speed test and load looks like this
Note the much improved CPU usage. That upload is way low but after turning off IPS I got an even worse run and then a slightly better one which makes me wonder if the speed tests are telling me anything. External factors must be throwing them off or something is causing flux in the OPNsense box I can't see.
Note the CPU usage has actually gone up even though IPS is now off which makes no sense at all.
Web GUI seems to have gotten slugish after enabling IPS even when traffic and CPU is low. eventually the dropped packets got so bad I rebooted but it did not seem to help so as a last ditch attempt I repovered the box after checking the cards were all well seated. This seems to have helped at least for now. Speedtest with IPS off
And Speedtest with IPS back on.
Doing more research Seeing 0% packet loss after repower but back to 20% and other weirdness within an hour.
Swapped out the 1 PCIe x1 network card (WAN side) and the 2 PCI cards (the slots the mother board had open) with a 4 port PCIe x4 card in place of the unneeded video card in the PCIe x16 slot and things have improved a lot! The next morning I was still seeing 0% packet loss and higher speeds than I had connected to the modem directly.
Last night I even hit over 40 Mbps up.
This is with these plugins installed
| os-acme-client (orphaned) | 1.13 | 221KiB | Let's Encrypt client |
| os-dyndns (orphaned) | 1.6_1 | 134KiB | Dynamic DNS Support |
| os-intrusion-detection-content-snort-vrt (orphaned) | 1.0 | 12.4KiB | IDS Snort VRT ruleset |
| os-smart (orphaned) | 1.2 | 15.9KiB | SMART tools |
And IPS on with the same ET and Snort rule sets as before.
Update: 5/17/2018 This are looking better though the results to vary a good bit.
Update: 5/17/2018 This are looking better though the results to vary a good bit.
Some of that might be from all that else is going on though. For instance here
There is about 40 mbps down and 5-6 mbps up going on besides the speed test. The fastest download test I was only seeing 8 mbps up because of how fast the security cams were triggering and transferring alert pics to the cloud that day.
I also added a Pi-Hole DNS filter which has shifted some load from Chrome and the OPNsense. To give you an idea here is the dashboard showing the number of DNS requests it is handling.
Simple to set up with these instructions. Just in time too as the ad blocker Chrome extension I had been using got caught doing stuff.
Short, quick and simplest version of install:
command line commands in bold-italicsFormat SD card with SDFormatterv4
Get NOOBS OS installer as zip
Copy NOOBS zip contents to SD card
Boot rpi with SD
Install Raspbian
When done ssh from another PC
ssh pi@192.168.0.62 (password raspberry)
or open terminal window on the pi's console
Run command
sudo raspi-config
Change the password
Optionally change the host name.
Switch to root user
sudo bash
and run these commands
apt-get update
apt-get upgrade
wget -O basic-install.sh https://install.pi-hole.net
bash basic-install.sh
Note password at end of line
[i] Web Interface password:
you will need it to login to the admin web interface.
Lastly you should backup your config any time you make changes like adding sites to a whitelist. If you are recovering from a crash (this has happened a couple times to me) you can also import your config from this screen (Settings->Teleporter) as well.
Update 7/7/2019 If you have Unifi
Check out [Step-By-Step Tutorial/Guide] Raspberry Pi with UniFi Controller and Pi-hole from scratch (headless) Easy setup, about the same cost as a Cloudkey Gen 1, About half that of a Gen2, works slick and can give you the space to turn on recording of Clients Historical Data that is tough on a Cloudkey Gen 1. My Raspberry Pi 3B+ seems to have no problem running both programs. I did bump the SD to 32GB. I've just turned on recording of Clients Historical Data so we'll have to see how much storage gets taken up by that.
Update 8/5:
After running the Unifi controller / Pi-hole combo for a couple weeks I'm getting a bit concerned. It has crashed twice now drastically degrading network performance since DNS goes offline. I had planned on taking the original Pi-hole offline but now I'm thinking I need to keep it up and config it as a backup.
Update 12/27:
Between logs, the Pi-Hole DB, the Unifi backups and the update files SD card keeps filling up regularly.
For example I had all these files over 100 MBs after doing some clean up
root@UnifiPi:/etc/pihole# find / -size +100M -ls |
287694 138240 -rwxr-xr-x 1 root root 141550912 Jul 10 07:27 /usr/lib/chromium-browser/chromium-browser
398403 122876 -rw-r--r-- 1 root root 125817618 Oct 18 13:28 /usr/lib/jvm/java-11-openjdk-armhf/lib/modules
278090 123076 -rw-r--r-- 1 root root 126023659 Oct 18 13:28 /usr/lib/jvm/java-11-openjdk-armhf/jmods/java.base.jmod
1582114 10821252 -rw-r--r-- 1 pihole pihole 11080900608 Dec 27 20:03 /etc/pihole/pihole-FTL.db
1835088 318560 -rw-r----- 1 root adm 326197642 Dec 2 00:00 /var/log/daemon.log.1
1835105 979680 -rw-r----- 1 root adm 1003184946 Dec 27 19:43 /var/log/daemon.log
1835084 277436 -rw-r--r-- 1 pihole pihole 284087304 Dec 1 00:05 /var/log/pihole.log.1
1835011 287236 -rw-r----- 1 root adm 294126053 Dec 27 20:00 /var/log/syslog
662490 131076 -rw------- 1 unifi unifi 134217728 Sep 5 09:38 /var/lib/unifi/db/_tmp_repairDatabase_last/ace_stat.3
662484 131076 -rw------- 1 unifi unifi 134217728 Oct 14 23:33 /var/lib/unifi/db/_tmp_repairDatabase_last/_tmp_repairDatabase_7/ace_stat.3
662486 262144 -rw------- 1 unifi unifi 268435456 Oct 14 23:33 /var/lib/unifi/db/_tmp_repairDatabase_last/_tmp_repairDatabase_7/ace_stat.4
662483 524036 -rw------- 1 unifi unifi 536608768 Oct 14 23:32 /var/lib/unifi/db/_tmp_repairDatabase_last/_tmp_repairDatabase_7/ace_stat.5
662497 131072 -rw------- 1 unifi unifi 134217728 Nov 4 03:47 /var/lib/unifi/db/_tmp_repairDatabase_last/_tmp_repairDatabase_5/ace_stat.3
662499 262144 -rw------- 1 unifi unifi 268435456 Nov 4 03:47 /var/lib/unifi/db/_tmp_repairDatabase_last/_tmp_repairDatabase_5/ace_stat.4
662496 524032 -rw------- 1 unifi unifi 536608768 Nov 4 03:46 /var/lib/unifi/db/_tmp_repairDatabase_last/_tmp_repairDatabase_5/ace_stat.5
662501 262144 -rw------- 1 unifi unifi 268435456 Sep 5 09:38 /var/lib/unifi/db/_tmp_repairDatabase_last/ace_stat.4
662489 524036 -rw------- 1 unifi unifi 536608768 Sep 5 09:37 /var/lib/unifi/db/_tmp_repairDatabase_last/ace_stat.5
662506 131072 -rw------- 1 unifi unifi 134217728 Dec 27 19:59 /var/lib/unifi/db/ace_stat.3
662503 131072 -rw------- 1 unifi unifi 134217728 Dec 27 20:02 /var/lib/unifi/db/ace.3
662527 131076 -rw------- 1 unifi unifi 134217728 Nov 25 13:15 /var/lib/unifi/db/_tmp_repairDatabase_1/ace_stat.3
662529 262144 -rw------- 1 unifi unifi 268435456 Nov 25 13:15 /var/lib/unifi/db/_tmp_repairDatabase_1/ace_stat.4
662526 524036 -rw------- 1 unifi unifi 536608768 Nov 25 13:13 /var/lib/unifi/db/_tmp_repairDatabase_1/ace_stat.5
662520 262148 -rw------- 1 unifi unifi 268435456 Dec 27 20:00 /var/lib/unifi/db/ace_stat.4
662519 262148 -rw------- 1 unifi unifi 268435456 Nov 25 23:59 /var/lib/unifi/db/ace.4
662464 131072 -rw------- 1 unifi unifi 134217728 Nov 22 00:04 /var/lib/unifi/db/_tmp_repairDatabase_0/ace_stat.3
662466 262148 -rw------- 1 unifi unifi 268435456 Nov 22 00:05 /var/lib/unifi/db/_tmp_repairDatabase_0/ace_stat.4
662463 524036 -rw------- 1 unifi unifi 536608768 Nov 22 00:04 /var/lib/unifi/db/_tmp_repairDatabase_0/ace_stat.5
662505 524036 -rw------- 1 unifi unifi 536608768 Dec 27 17:06 /var/lib/unifi/db/ace_stat.5
662515 131072 -rw------- 1 unifi unifi 134217728 Nov 29 00:05 /var/lib/unifi/db/_tmp_repairDatabase_2/ace_stat.3
662517 262144 -rw------- 1 unifi unifi 268435456 Nov 29 00:05 /var/lib/unifi/db/_tmp_repairDatabase_2/ace_stat.4
662514 524036 -rw------- 1 unifi unifi 536608768 Nov 29 00:03 /var/lib/unifi/db/_tmp_repairDatabase_2/ace_stat.5
662675 262144 -rw------- 1 mongodb nogroup 268435456 Jun 30 2019 /var/lib/mongodb/journal/prealloc.2
662677 262144 -rw------- 1 mongodb nogroup 268435456 Jun 30 2019 /var/lib/mongodb/journal/prealloc.1
662676 262144 -rw------- 1 mongodb nogroup 268435456 Dec 27 18:37 /var/lib/mongodb/journal/j._0
4194815 178776 -rw-r--r-- 1 root root 183066184 Oct 22 23:08 /var/cache/apt/archives/openjdk-11-jdk-headless_11.0.5+10-1~deb10u1_armhf.deb
4194330 172596 -rw-r--r-- 1 root root 176736120 Jun 25 2019 /var/cache/apt/archives/openjdk-11-jdk-headless_11.0.3+7-5_armhf.deb
So I'm swapping the SD to a 128GB one using these instructions. Note if you installed via nobs like I did you will need to use the instructions to make a new partition instead of expanding root. I used these variations:
parted
mkfs.ext4 /dev/mmcblk0p3
e2label /dev/mmcblk0p3 var
vi /etc/fstab
/dev/mmcblk0p3 /var2 ext4 defaults 1 2
mkdir /var2
mount /var2
vi /etc/fstab
/dev/mmcblk0p3 /var ext4 defaults 1 2
mkdir /vb
systemctl stop unifi.service
/etc/init.d/pihole-FTL stop
cd /var
find . | cpio -pvmd /var2
cd /
mv /var /vb
mkdir /var
mount /var
Then just to be sure
df
New FS should show up as /var
reboot
Everything should not restart OK and you can start deleting stuff from /vb
This gets Unifi and Pi-Hole in separate file systems. Mine came out like this
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/root 28776316 25388648 1902868 94% /
devtmpfs 469544 0 469544 0% /dev
tmpfs 474152 1580 472572 1% /dev/shm
tmpfs 474152 6488 467664 2% /run
tmpfs 5120 4 5116 1% /run/lock
tmpfs 474152 0 474152 0% /sys/fs/cgroup
/dev/mmcblk0p3 91611060 12665804 74248568 15% /var
/dev/mmcblk0p6 258094 53035 205060 21% /boot
tmpfs 94828 0 94828 0% /run/user/1000
tmpfs 94828 0 94828 0% /run/user/999
Update 3/6/2020: Still running out of space on / which causes the Pi to crash
This is caused by /etc/pihole/pihole-FTL.db getting huge. Mine was 15,561 MB when the system ran out of space.By default the DB keeps up to a years worth of data. You can either reduce this by adding MAXDBDAYS to /etc/pihole/pihole-FTL.conf to reduce the days or probably better solution moving the db onto the /var partition created earlier. To do that add DBFILE=/var/pihole/pihole-FTL.db to /etc/pihole/pihole-FTL.conf then run
mkdir /var/pihole
/etc/init.d/pihole-FTL stop
cp /etc/pihole/pihole-FTL.db /var/pihole/
Note this takes awhile. (My 15 GB file took about 30 minutes!) Once it is done:
/etc/init.d/pihole-FTL stop
ls -lapi /var/pihole/
Once you see it is updating the DB you can remove the old DB with
rm /etc/pihole/pihole-FTL.db
Now I have a lot more space on root and /var hardly sees the increase.

































Updated with info from Quad Core server swap
ReplyDeleteUpdated with new network card info
ReplyDeleteUpdated with Pi-Hole info
ReplyDelete